preface
本篇文章是 picoCTF 2018 Web 部分的 writeup,持续更新中
Inspect Me
Question
Inpect this code! http://2018shell.picoctf.com:53213
Hint
(1) How do you inspect a website’s code on a browser?\
(2) Check all the website code.
Solution
送分题,Ctrl + U 查看源代码,得到一部分 flag : picoCTF{ur_4_real_1nspe ,按开发者按钮 F12 进入 mycss.css 得到另外一半 flag : ct0r_g4dget_402b0bd3}
Client Side is Still Bad
Question
I forgot my password again, but this time there doesn’t seem to be a reset, can you help me? http://2018shell.picoctf.com:53990
Hint
(1) Client Side really is a bad way to do it.
Solution
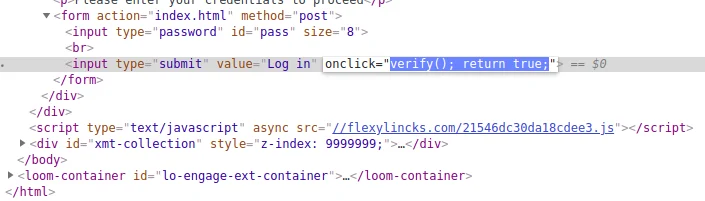
这题上去就是一个登录框,F12 对这个按钮进行检查,发现调用了一个函数,搜索这个函数的定义就拿到 flag 了,所以千万不要把密码保存在客户端上

Irish Name Repo
Question
There is a website running at http://2018shell.picoctf.com:52135 . Do you think you can log us in? Try to see if you can login!
Hint
(1) There doesn’t seem to be many ways to interact with this, I wonder if the users are kept in a database?
Solution
开始还不知道这题要干什么,点进连接后可以看到一个 Admin Login 的选项卡,点进去是个用户登录界面

尝试 admin 123456,失败,那就对网络请求进行分析,也没有看到有关 cookie ,结合题目内容,应该是想让我们用 sql注入,那就尝试注入,填入 Username 为 ' OR '1'='1' -- ,这样的话会把后面的 sql 语句给忽略,如果看不懂的话可以去了解一下 sql 语句 和 sql注入 ,Password 随便填一个,这里它没有对输入进行检查,所以不填密码都行,点击按钮提交就能拿 flag 。
Mr. Robots
Question
Do you see the same things I see? The glimpses of the flag hidden away? http://2018shell.picoctf.com:15298
Hint
(1) What part of the website could tell you where the creator doesn’t want you to look?
Solution
就是个 robots 协议 题目,登上 http://2018shell.picoctf.com:15298/robots.txt 会得到输出
User-agent: *
Disallow: /c4075.html
说明服务器禁止(并不能)访问 /c4075.html 这个文件,然后我们访问一下这个文件就拿到 flag 了。
Buttons
Question
There is a website running at http://2018shell.picoctf.com:18342 . Try to see if you can push their buttons.
Hint
(1) What’s different about the two buttons?
Solution
这题刚开始给了一个按钮,分析一波通过 POST 方法提交表单转到 button1.php ,然后 button1.php 又有一个超链接(button2),点击之后重定向到了 boo.html,开始播放视频,并且页面显示 FORM DISABLED. THIS INCIDENT HAS BEEN LOGGED AND REPORTED TO /dev/null ,我还 ssh 登录到服务器上去看 /dev/null 里面有没有 flag (I’m so vegetable)
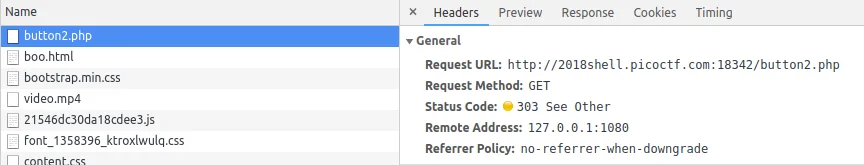
实在找不到哪里有破绽,只好去搜别人的 writeup, 结果发现只要把第二个请求变成 POST 就拿到 flag 了(因为默认是 GET 请求所以被重定向了),不过学习到了一个很好用的命令行 HTTP 工具 叫做 HTTPie ,直接在命令行就能发送各种请求,不用我自己写爬虫了。

Logon
Question
I made a website so now you can log on to! I don’t seem to have the admin password. See if you can’t get to the flag. http://2018shell.picoctf.com:37861
Hint
(1) Hmm it doesn’t seem to check anyone’s password, except for admins?
(2) How does check the admin’s password?
Solution
分析一波,不管填什么都能正确登录,检查 Cookie 发现 admin一直是 False,那就给个 True 值发送给 flag 页面,拿到 flag
$ http http://2018shell.picoctf.com:37861/flag Cookie:admin=True | grep pico

Secret Agent
Question
Here’s a little website that hasn’t fully been finished. But I heard google gets all your info anyway. http://2018shell.picoctf.com:3827
Hint
(1) How can your browser pretend to be something else?
Solution
从题目上来说就是要改变我们浏览器的 User-Agent 让它伪装成 google , 以为是挺简单的一件事,直接将 User-Agent 修改成 google 然后去访问网页,然后,没卵用

http GET http://2018shell.picoctf.com:3827/flag 'User-Agent:google'
看了 writeup 再去看一遍题目,应该是说这个网站还没有建完,但是 Google 爬虫依然可以抓到这个网站的信息,所以应该将 User-Agent 修改成 Google 爬虫的 User-Agent ,搜索了 Google 爬虫的 User-Agent 再更换就可以了
$ http GET http://2018shell.picoctf.com:3827/flag 'User-Agent:Mozilla/5.0 (Linux; Android 6.0.1; Nexus 5X Build/MMB29P) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.96 Mobile Safari/537.36 (compatible; Googlebot/2.1; +http://www.google.com/bot.html)'
No Login
Question
Looks like someone started making a website but never got around to making a login, but I heard there was a flag if you were the admin. http://2018shell.picoctf.com:33889
Hint
(1) What is it actually looking for in the cookie?
Solution
哭了,这题竟然也是跟上面那题一样的,只需要在请求中发送 cookie , 让 admin=1 就行了,看了别人的 writeup 才知道
$ http GET http://2018shell.picoctf.com:33889/flag "Cookie:admin=1"
demo
Question
demo
Hint
demo
Solution